Robert Muller, the sixth director of the FBI, is quoted as saying, “I am convinced that there are only two types of companies: those that have been hacked and those that will be. And even they are converging into one category: companies that have been hacked and will be hacked again.”
If you take Robert Muller’s idea seriously, you’ll likely come to the conclusion that it’s time to start investigating your company to find out which of the two categories it belongs to: “those that have been hacked” or “those that will be.” This sort of investigation is called threat hunting.
Most security teams focus on implementing and improving security controls and systems that detect attackers’ actions – and responding when indicators of a threat are identified on the enterprise network.
This is central to security implementation. However, sophisticated adversaries use persistent methods that work for weeks, months, or even years – in their attempts to get their hands on valuable data or disrupt business operations. Eventually, a sophisticated hacker is likely to succeed. So, what happens next?
Threat Hunting Defined
The goal of threat hunting is to reduce the time between a breach and its discovery. This is achieved by proactively searching and discovering cyber threats and vulnerabilities.
Hunters start by assuming their organization already has been hacked. They view their job as confirming or refuting this first basic hypothesis – by hunting for evidence, before damage can occur.
But how do you search for the unknown? How do you know if whatever it is that you found – is what you were looking for?
Threat hunting is the process of actively looking for signs of malicious activity within enterprise networks, but without prior knowledge of those signs.
Threat hunting is the process of actively looking for signs of malicious activity within enterprise networks, but without prior knowledge of those signs. It involves uncovering malicious activity that does not trigger alerts; the kind of malware that you cannot catch with the currently known signatures.
Myths and Facts
Most non-hunters think that threat hunting means taking known Indicators of Compromise (IoCs) from threat intelligence feeds – and searching for them.
While it is valuable to know if you are susceptible to previously discovered attacks, this kind of retrospective approach is akin to driving down a road while looking only in the rearview mirror.
Another misconception is that threat hunting relies mostly on automatic detection and hunting technologies. This is not true; threat hunting relies primarily on human processes.
Existing technologies are critical enablers, allowing hunters to capture, identify, correlate, enrich, measure, and analyze the thousands of pieces of data that are needed to conduct effective hunts. But those technologies do not replace the hunters.
The Importance of the Right Hypothesis
Threat hunting involves hypothesizing about attackers’ behavior, then verifying the hypotheses in your environment. That’s when the threat hunting team needs to think like a threat actor, using techniques and tactics that adversaries could possibly use against the organization.
Although techniques and tactics are sometimes treated as synonyms, they are not. Think of techniques as aspects of a threat actor’s skill set; while tactics are the application of those techniques.
Keep in mind that adversaries are not constrained in the ways that defenders are, and some adversaries operate in more than one threat category.
Adversaries are not constrained in the ways that defenders are, and some adversaries operate in more than one threat category.
What Guides the Hunt?
Cyber threat intelligence is critical in the process of developing a hypothesis. If we know that attackers are going to follow specific steps, we can hunt in parts of the computing environment that could be expected to show traces of these actions.
It’s too hard to hunt without having any clues of where or what you’re looking for.
This is particularly true because advanced attacks are so complex: Often, they combine multiple discrete techniques and occur over relatively compressed time periods. They can include both benign and malicious executables and acquire some type of privileged access. Moreover, they may involve one or more endpoints and change the contents of endpoint file systems.
Threat intelligence focuses the organization’s resources on the most relevant threats and vulnerabilities and can save a threat hunting team huge amounts of time.
An Attack Life Cycle Framework Helps Hunters Be More “On Target”
Before defining individual threat hunts and hypotheses, it is useful to adopt an attack life cycle framework that breaks down the phases of a typical cyber attack and the techniques it might use in each phase.
There are many frameworks available within the InfoSec community, including the Cyber Kill Chain® coined by Lockheed Martin, Malone, UKC, Laliberte, Nachreiner, and Mandiant’s Attacker Life Cycle Model.
At CyberProof, we have adopted a framework that we believe is the most mature – MITRE’s Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK™) framework, which has become a standard in the InfoSec industry. The MITRE ATT&CK goes into more depth than most of the others, and its details on post-compromise attacker techniques provide useful guidance on where, what, and how to hunt for the evidence.
The matrix lists the following tactics: Initial Access, Execution, Persistence, Privilege Escalation, Defense Evasion, Credential Access, Discovery, Lateral Movement, Collection, Exfiltration, and Command and Control:
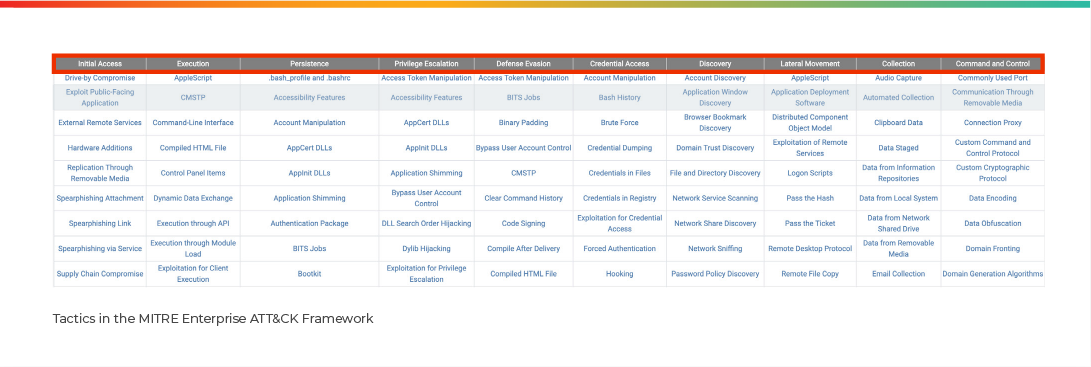
For each tactic, there is a list of known techniques:
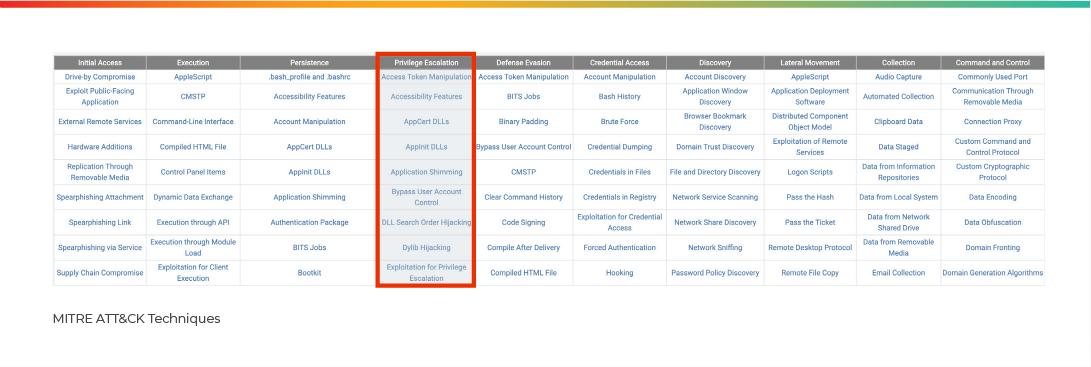
ATT&CK isn’t limited to one type of adversary, but instead provides threat-agnostic techniques that are relevant to any threat. Frameworks like MITRE’s ATT&CK help threat hunters apply a threat-agnostic approach and hunt for the hypothesis that is most accurate and most relevant.
It is worth taking the time to select or build an attack lifecycle framework to guide your hunt. It will help your threat hunting team think like attackers and stay focused on the attack techniques that are most likely to be used against your organization. You can add to an existing framework or combine elements of several frameworks to create a custom framework of your own – because no one knows your environment like you do.
Putting it all Together
Hunt teams are at the core of threat hunting efforts. Relying primarily on human processes, hunt teams are focused on uncovering attacker behaviors and identifying other evidence of attacker techniques and activities.
A hunt team should have the skills to utilize a broad range of security methods and tools: incident analysis and response, detection and analysis of attacks, knowledge of malware and exploits, and analysis of data from multiple sources. They also should document their findings because this can form the basis for legal action at a later stage.
A team that hunts and mitigates threats generally includes an incident manager, response analyst, threat intelligence analyst, malware analyst, and the operations staff.
Threat Hunters Protect Your Business
Technically speaking, threat hunting aims to limit the time between the infection of a network and its detection. This is crucial in giving an organization the ability to respond to an attack before it has an impact and effects a business.
Typically, an organization will only discover an attack 6 months after the initial infection takes place. By then, it might be too late – the damage may have been done.
The key to good threat hunting is the people.
The key to good threat hunting is the people. Integrate really good people from different disciplines and work with individuals who have true expertise to successfully run a coordinated, enterprise-wide response.
Finally, using a framework such as the MITRE ATT&CK™ helps threat hunting teams think like threat actors so they can come up with the correct hypotheses and figure out threat actors’ techniques and tactics. Use of an appropriate framework contributes to faster and more effective incident detection and response – and, ultimately, improves your cyber resilience.
If you want to find out more, contact an expert or download our MITRE ATT&CK Framework Whitepaper.



