CyberProof’s analysts have discovered that WSH RAT was leaked on a prominent deep web hacking forum. The leak took place on September 17.
About WSH RAT
WSH RAT is a new variant of Houdini Worm that was detected in the wild in June 2019, targeting commercial banking customers, and whose volume of infections increased throughout the past months.[1] The RAT is usually distributed through malspam emails within a malicious attachment, and it features a large variety of remote access, evasion, and stealing capabilities.
Here’s some of what we’ve learned about this latest cyber security threat and how the leak happened:
WSH RAT is being traded on a deep web forum
On June 2, 2019, a threat actor posted on a cybercrime deep web forum that he is selling the WSH RAT builder by subscription. Customers who pay $50 per month can unlock it. The builder has been heavily promoted online with many positive comments and a high level of reliability.
WSH RAT is still active
Since then, the RAT has been spotted in multiple phishing attacks, probably operated by the buyers of the traded RAT builder. Notably, during the past week security researchers reported on recent WSH RAT infections via malspam within a malicious attachment.[2] The attachment contained an MHT file containing an href link which, when opened, directed victims to a .zip archive containing a version of WSH RAT.
On September 17, 2019, our cyber security threat intelligence team detected the leak of the “WSH Rat V2.0” tool on another prominent deep web hacking forum. The leaked tool was published by a forum member, who “cracked” the paid version and shared the tool for free.
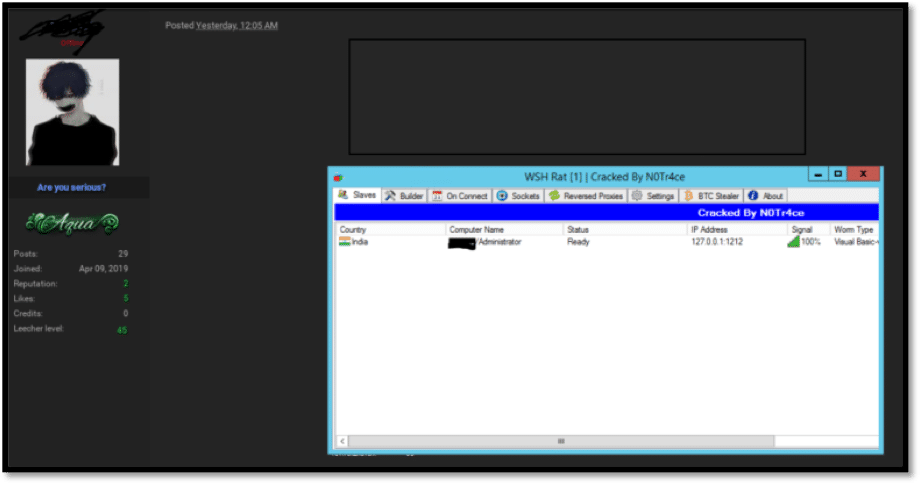
So far, the underground post was viewed and was commented on by many forum members, who highly appreciate the tool being shared. We assume that the fact that WSH RAT is now available and accessible for free will enable a variety of threat actors, including less skilled actors, to mount cyber attacks and will lead to a significant increase in malspam campaigns distributing this malware strain in additional cybercrime campaigns.
Mitigation Steps
We recommend implementing the following IOCs and launching an internal awareness campaign warning employees against opening files from unknown sources.
Below is list of indicators of compromise (IOCs) associated with the recent malware activity.
Domains
galakhov.duckdns[.]org
pluginsrv1.duckdns[.]org
motwani.duckdns[.]org
ijehawele.duckdns[.]org
dbin240.ddns[.]net
unknownsoft.duckdns[.]org
mxrecords9688.bounceme[.]net
IP Addresses
45.79.48[.]200
79.134.225[.]83
192.185.26[.]103
192.185.163[.]240
23.105.131[.]191
23.105.131[.]225
185.247.228[.]49
165.22.129[.]173
165.22.213[.]154
185.62.190[.]105
185.194.141[.]58
79.134.225[.]72
91.132.139[.]181
YARA rule and additional malware hashes can be found in the following link:
https://github.com/jeFF0Falltrades/IoCs/blob/master/Broadbased/wsh_rat.md
We urge our clients to take all the necessary precautions.