What does it take to be a threat hunter, who works proactively to uncover hidden threats lurking inside an IT network?
Threat hunters rely on a blend of both offensive and defensive skills, and adopt a mindset that involves knowing how the attack chain works and how to develop new capabilities. They understand sophisticated adversarial methods and know how to defend the enterprise — protecting an increasingly complex environment and understanding its architecture, how it operates, and what to look for to build out a strong threat hypothesis.
To do their work effectively, alongside the ability to make smart judgment calls and follow the thread of intuition, threat hunters rely on a wide range of data. To find the attacker that may be lurking in the data, there are tools that can point in the right direction - and that utilize automation to scale the hunting process and reduce hunting time.
Threat hunters understand sophisticated adversarial methods and know how to defend the enterprise — protecting an increasingly complex environment and understanding its architecture, how it operates, and what to look for to build out a strong threat hypothesis.
Understanding the Pyramid of Pain
When used correctly, the right tools and techniques come together to support a threat hunting team with increasingly sophisticated activities. Threat hunters escalate through what’s known as the Pyramid of Pain. This is a security concept which explains how different kinds of security controls impact an attacker.
For threat hunters, as you move up the pyramid of pain, you make it more difficult and more frustrating for attackers to evade detection and successfully attack the environment.
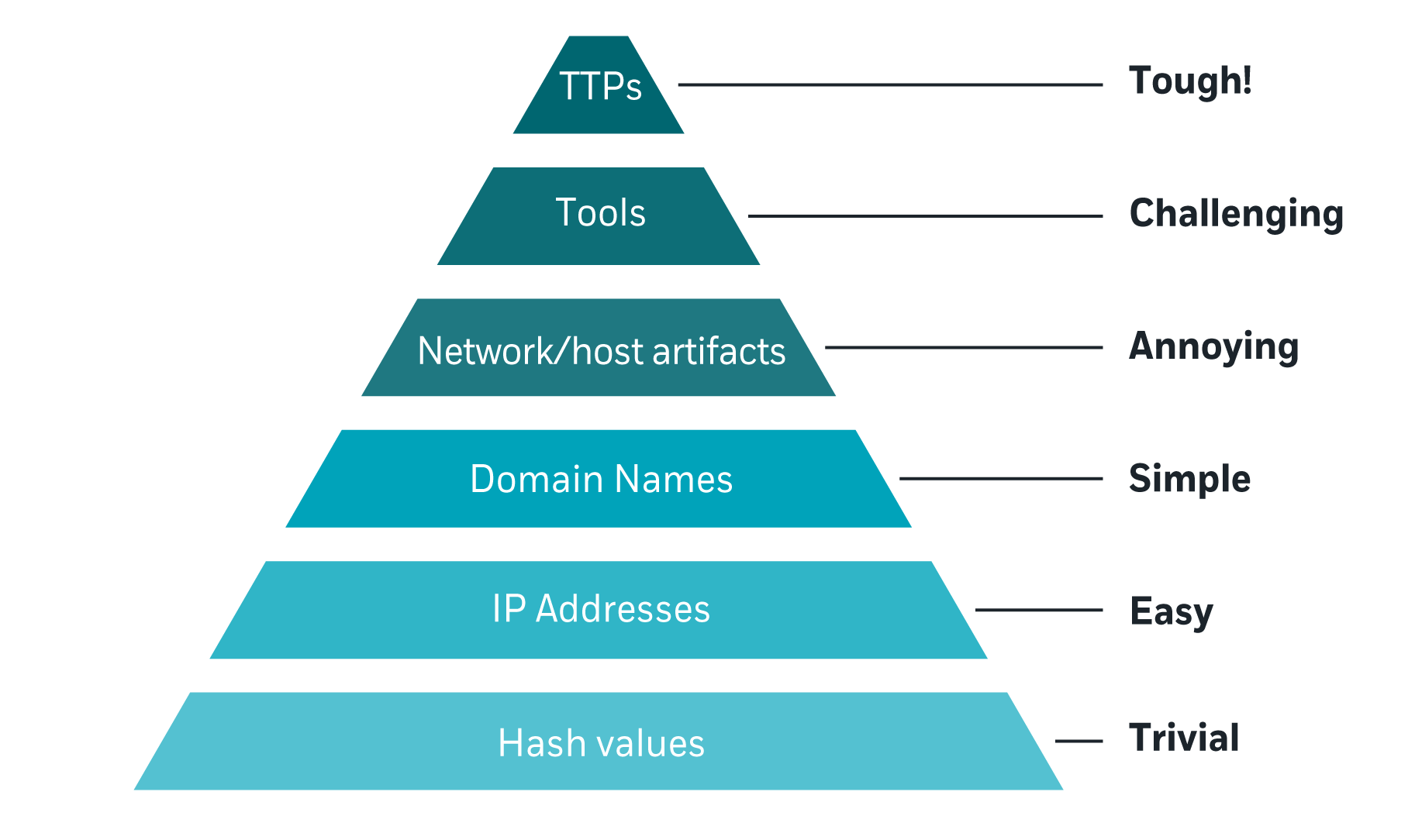
As you can see in the pyramid, when threat teams search for malicious intent by looking for hash values, IP addresses, and domain names that correspond to known attacks - i.e., the lowest three layers of the triangle - their impact is limited. It is relatively simple for attackers to avoid specific hash values, IP addresses and domain names, and so this causes them little concern.
However, once the threat team starts to identify attacker behavior in more granular detail, things get harder for the threat actors. The next level of the pyramid involves network host artifacts, examples of which could be URI patterns, C2 information embedded in network protocols, and distinctive HTTP User-Agent or SMTP Mailer values. These can be distinguished by threat hunting teams from legitimate behavior and put the spotlight on the attacker.
If threat hunting teams can move up to the top of the pyramid, where they can uncover the hackers’ tools and Tactics, Techniques and Procedures (TTPs), success becomes far more difficult for the attacker. This is partly because hashes, IPs and domains are relatively dynamic and can be quickly changed or established per targeted attack. However, TTPs and tools are more stable. If they have a high success rate, threat actors will be less likely to change them.
Common Hunting Tools
Hackers are continually developing their own tools, and the more advanced the attack, the harder these are to track. For threat hunters to understand and monitor TTPs, they must grasp not only how attackers have achieved initial access, but what they are most likely to do next.
For threat hunters to understand and monitor TTPs, they must grasp not only how attackers have achieved initial access, but what they are most likely to do next.
To support these threat hunting initiatives, common tools most likely to be used by threat hunters include:
-
SIEM: Security Information and Event Management (SIEM) tools bring together many data sources into a single view. In one place, threat hunters can review firewall logs, email logs, DNS and proxy logs, and more. SIEM tools will usually choose pertinent data from other areas depending on the organization’s decisions around data retention, cost, and which data sources to onboard, and so may not provide as much depth as looking at these areas directly.
-
EDR/XDR: Endpoint Detection & Response (EDR) provides a greater amount of information about the endpoint, such as changes to the operating system or hooking into system components for more in-depth visibility. eXtended Detection & Response (XDR) takes this further and extends visibility to other areas, such as the network and email gateways, connecting additional dots.
-
Security products: Most organizations will have data coming from additional tools, both cloud and on-prem., such as antivirus alerts, information direct from the firewall, or anti-malware or ransomware tools. Gaining access to the data from these tools can provide more in-depth information for the hunters. In a hybrid reality, cloud app security adds information such as cloud infrastructure data, cloud application data, cloud identity and access, and audit and compliance data. Additional data from security tools can be useful if you don’t have a SIEM, if data is not being shipped to your SIEM, or if you want a more elaborate dataset than the SIEM provides.
Common Hunting Techniques
With these tools, and depending on the goals of the hunt, the threat hunting team uses a variety of different techniques when dealing with large volumes of data:
-
Hunters may manually search for evidence if they know what they are looking for — such as a malicious IP address. They could group common indicators together such as the file path, network port, or grouping by host, to perform investigation on many files at once.
-
Another technique is stack counting, in which the threat hunter can see information based on what’s common and what’s unique, counting the number of occurrences for values of a particular type, and analyzing the outliers or extremes. By stack counting all ports, for example, a threat hunter could uncover that an unusual port has a number of events related to it — triggering further investigation.
-
Finally, there are techniques based on Machine Learning, such as Clustering is similar to grouping - but with clustering, teams can uncover common indicators which may be less obvious to the human eye. Machine Learning can discover connections between data by leveraging unfamiliar properties which may otherwise slip under the radar.
Using open-source tools to complement threat hunting
Open-source tools are a powerful category of technology in a threat hunter’s arsenal. These tools and scripts could be incorporated with automation elements of a hunt, and are easily modified - so they are customizable to fit the needs of the threat hunting team.
Usually developed and maintained by a community or security companies, open-source tools often have the benefit of having a wide group of users who are continually enhancing and iterating to get the best out of the technology, and share “best practices” across the cybersecurity community. When faced with a growing threat, the community can work together to find the best solutions, sharing what’s tried and tested in their own environment. Security researchers also gain knowledge from these tools, and take inspiration to develop their own custom tools and improve existing ones.
Usually developed and maintained by a community or security companies, open-source tools often have the benefit of having a wide group of users who are continually enhancing and iterating to get the best out of the technology, and share “best practices” across the cybersecurity community.
Protecting Enterprises Against Fileless Attacks
One example of a growing threat in today’s IT environments is fileless attacks, as threat actors attempt to infect a network while leaving behind the least amount of evidence possible and evading security defenses - gaining privilege escalation, leaking information and more.
One example of a growing threat in today’s IT environments is fileless attacks, as threat actors attempt to infect a network while leaving behind the least amount of evidence possible and evading security defenses - gaining privilege escalation, leaking information and more.
The three most common approaches for fileless attacks are:
-
Windows Registry: Deploying code into the registry storage
-
Memory Injections: Injecting code into running process’ memory
-
Scripting: Using scripting languages (such as PowerShell or VBScript) to carry out malicious activities without the need for additional files to be written on the disk. .
As part of protecting organizations against fileless attacks, at CyberProof we leverage two powerful open-source tools. We learn from them, conduct research to evolve and improve them, and take inspiration from these tools to enhance our own tools and hypotheses: MEMHUNTER and REG-HUNTER.
Live hunting of code injection via MEMHUNTER
This open-source tool is an endpoint sensor tool which performs live memory forensics, and improves threat hunter analysis by automatically detecting resident malware living in Windows processes. Unlike other approaches which rely on taking a snapshot of the memory and then conducting forensics on that offline snapshot, MEMHUNTER does not rely on memory dumps, making it much less resource-intensive. MEMHUNTER can run in real time and at scale on machines, with no human intervention, to look for suspicious events which are occurring in the memory, including process, DLL, PE, and thread injection, process hollowing and more.
We love this tool because it’s efficient, highly scalable, and very feature rich. MEMHUNTER also provides tools to simulate process injection attacks, which we can use for learning, as well as testing the MEMHUNTER tool itself.
Registry triage and hunting via REG-HUNTER
REG-HUNTER is another open-source tool that performs a similar role for live registry hunting, running across the specific endpoints defined by the threat hunting team. The open-source tool scans Windows Registry and looks for various suspicious activities: from Shell and encoded commands, to the presence of sensitive information such as passwords, users, IP addresses or URLs.
This tool is a great asset for our threat hunting team due to how comprehensive and diverse it is.
Building on open-source tools
It’s important to remember that no tool can solve all of your needs, and no tool should just be used out of the box. We always advise that threat hunters take open-source tools like these as inspiration — to learn how they work and then use them to enrich your capabilities as a hunter. Build around them, and improve them so that they fit your contextual needs. And always remember to perform other traditional hunting techniques such as a manual review of the data.
One example of a tool that we use at CyberProof is our DensityScout File Scanner (DSFS), a custom tool we built around DensityScout, which looks for encrypted or packed files on an Operating System and can calculate the density of those files (which is similar to entropy).
Leveraging multiple tools to support advanced threat hunting
Combining and using multiple open-source utilities, such as DensityScout, SigCheck and PowerShell, CyberProof has created a more advanced tool which looks for dormant or live malicious file artifacts on endpoints and servers. Our script takes the capabilities of these open-source tools, and builds a wrapper around them to collect specific information and send that to our team. By utilizing machine leargning capabilities and a wealth of data, we trained a model to recognize malicious file properties versus clean files. Our tool can now predict the probability of malicious files from hundreds or even thousands of endpoints, with an accuracy level of between 80-90 percent.
The CyberProof Defense Center (CDC) platform can execute these tools remotely, or collect the information from the security teams during incident response, where necessary. On receipt of the information, this allows the Security Operations Center (SOC) team to enrich incident response processes with additional data, tools, and techniques that support the hunt.
Our tool can now predict the probability of malicious files from hundreds or even thousands of endpoints, with an accuracy level of between 80-90 percent.
If you’re interested in any of the tools that we’ve discussed in this article, you can find more information here. Don’t forget to join the conversation and let us know what you think!



