Since the Russian invasion into the Ukraine began, cyber warfare between the two countries has escalated with more and more campaigns, malware strains, and attacks having been observed against a variety of Ukrainian government organizations.
This post covers the latest updates in the cyber warfare between the two countries.
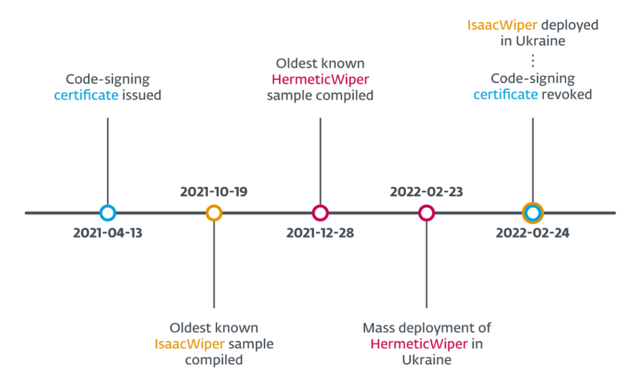
Timeline of Important Cyber Events in Russian-Ukrainian Cyber Warfare
Second Wiping Attack via IsaacWiper Observed
This new unattributed wiper was used in an attack against a Ukrainian government network just before Russia sent troops into the Ukraine, while a new version of it was observed in attacks the very next day. (Read more here.)
Of note is the fact that IsaacWiper was used in attacks against a network that was unaffected by HermeticWiper. Additionally, it’s suggested that attackers are finding ways to move laterally between networks, to further spread the malware.
It is currently unclear whether the two wipers are linked, as IsaacWiper is a far less sophisticated piece of malware (see WeLiveSecurity’s article).
Researchers indicate that while the method through which IssacWiper is delivered to victims is currently unknown, RemCom – a remote access tool – had been deployed at the same time as IsaacWiper attacks. They also mention that Impacket is possibly being used to move within the afflicted network, according to ESET. Thus, it is suspected that attackers utilizing IsaacWiper managed to infiltrate the target networks some time before the attacks took place.
HermeticWizard and HermeticRansom
Researchers spotted a new worm named HermeticWizard used to drop HermeticWiper with the help of WMI and SMB spreader modules. This was detected alongside the discovery of a Golang ransomware named HermeticRansom (also known as Elections Go Ransom and PartyTicket).(Read more on BleepingComputer here.)
The new ransomware was likely used as a smokescreen for the HermeticWiper attack due to its non-sophisticated style and poor implementation and was used to target assets on the same day HermeticWiper was distributed.
Researchers note that the HermeticRansom malware does not use any kind of obfuscation and has straightforward functionality, suggesting it was created in a short amount of time.

HermeticRansom ransom note
Researchers are moderately confident that the HermeticRansom malware is linked to HermeticWiper’s primary objectives – destroying or otherwise making Windows systems unusable due to data loss – given the circumstances under which it appeared.
FoxBlade
Researchers mentioned that Ukrainian networks and infrastructure was seen being targeted by a recently discovered malware mere hours prior the Russian invasion began, according to Microsoft.
While several researchers have noted that FoxBlade and HermeticWiper are one and the same, there seems to be discourse within the cybersecurity community regarding this issue. One primary difference between the two pieces of malware that seems to contribute to the confusion surrounding this matter is the fact that HermeticWiper was not observed to have DoS capabilities, while FoxBlade can deliver such an attack.
Recommendations
- Ensure all systems are properly patched to the latest version
- Organizations with ties to Ukraine should carefully consider how to isolate and monitor those connections to protect themselves from potential collateral damage.
- Implement a DNS security solution to detect and mitigate DNS requests for known C&C infrastructure
- Monitor for the creation of suspicious file modification activity, particularly large quantities of file modifications in user directories.
- Identify and limit directly accessible access points to a minimum necessary amount and monitoring access attempts and traffic sources for signs of anomalies.
- Implement and enforce multi-factor authentication for remote authentication.
- Recommendation for HermeticWizard: Monitor traffic on the ports HermeticWizard uses to worm through networks – ports 20, 21, 80, 135, 137, 139, 443, and 445.10
- Recommendation for HermeticRansom: Consider using the Go script in the following link for decryption purposes.
Interested in learning more about protecting your organization from cyber attack? Contact us!


