Millions of accounts are currently vulnerable to a cyber security threat known as Password Reset Man-in-the-Middle (MitM) attacks – a form of attack that allows even a relatively unsophisticated attacker to take over user accounts by exploiting poorly designed password reset procedures.
It works as follows: The attacker creates a malicious website, where victims “register” to receive free services, software, or a free download. When the victim starts entering personal information, the attack begins. The attacker uses the information provided during registration to take over a victim’s account on other websites.
MitM – Simple but Dangerous
The MitM password reset is an attack exploits the similarity of the registration and password reset processes to launch a man-in-the-middle attack at the application level.
The MitM password reset attack exploits the similarity of the registration and password reset processes to launch a man-in-the-middle attack at the application level.
The attacker needs basic information such as a username, email, phone number, and even personal information like the answers to security questions, such as the name of the victim’s mother or his or her pet – in order to initiate the “forgot my password” process on another website, in the victim’s name.
Gaining Control of a Victim’s Email Account
The morning paper blog highlights that an especially good target of MitM attacks is a user’s email account. Gaining control of an email account is significant step in gaining full access to a victim’s data and identity.
Once an attacker obtains a victim’s email address and initiates a password reset on an email service provider website, the attacker can forward every challenge from the email service provider to the victim. The victim, who isn’t even suspicious – is lulled into thinking the questions are part of the registration process for the new site.
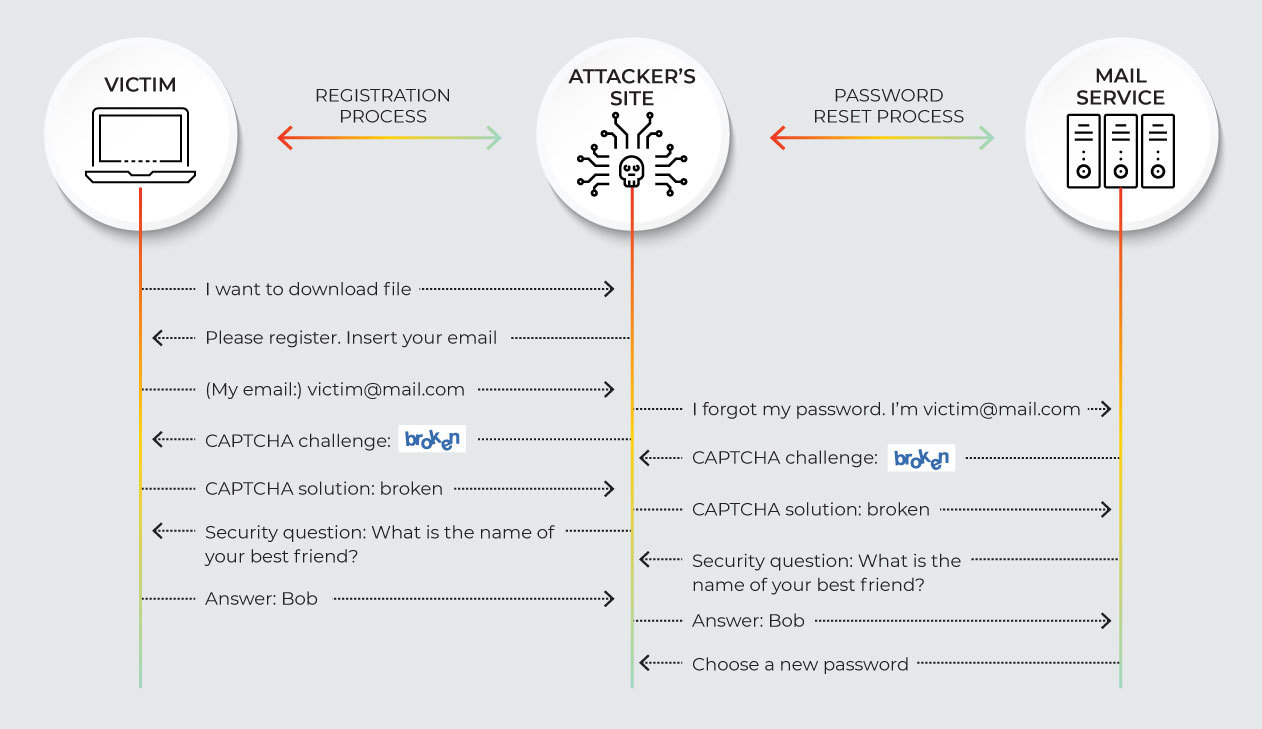
Information required for reset password processes typically includes CAPTCHA challenges, security questions, or a code sent to the victim’s mobile phone.
What about 2-Factor Authentication?
As pointed out by Ms. Smith on CSO Online, 2-factor authentication doesn’t reduce the risk of PRMitM (MitM password reset attacks). When the victim’s account, which the attacker is trying to take over, requires 2-factor authentication via mobile device, the attacker’s site asks for the victim’s phone number as part of the registration process.
2-factor authentication doesn’t reduce the risk of PRMitM (MitM password reset attacks)
You’d think the victim might notice that the security code sent to his or her phone comes from a different service. But it’s not that simple. It turns out SMS messages with codes are often not labeled with the name of the service that sent it.
Even when the name is there, frequently users aren’t paying enough attention. For one thing, they are anticipating receiving the code as part of the registration process. If they are very focused on copying the code and completing registration, they may not bother to read the rest of the SMS when the code pops up on the phone.
PRMitM Vulnerability is Insanely Widespread
Google is extremely vulnerable to PRMitM attacks that exploit the password reset process using a phone call. And Facebook is particularly vulnerable to PRMitM attacks through SMS messages. Yahoo!, LinkedIn, Yandex, and other email services also have vulnerabilities.
Facebook is particularly vulnerable to PRMitM attacks through SMS messages
It’s true that PRMitM attacks cannot be applied on websites that allow password reset only by sending a reset link to the email or using mobile push notification. This is of limited help, however, for attacks involving the email service providers themselves – where the email option is not relevant.
What’s the Answer?
Because PRMitM exploits server-side design bugs, there is little chance for users, or other client-side defenses (such as browser built-in mechanisms or extensions), to detect the attack.
However, PRMitM can be blocked by redesigning reset password processes – for example, by forcing users to understand when someone asks to reset a password.
It’s true that this might affect the user experience. However, in operations like password reset, it is reasonable to make users work harder to reset passwords – if it significantly improves security.
Being Smart About Security Questions and Phone Calls
Cyber security strategies and techniques in the reset password processes that can significantly reduce the risk of attack include:
-
Use better security questions: When a website asks many questions that are directly related to the actions done by the user on that site, these questions cannot be forwarded as legitimate security questions for other sites. For example, Google asks questions about common contacts, user-defined labels, and the use of Google services.
-
Adopt a smarter approach to phone calls: Phone calls can be secure if the message includes the name of the sender, an explanation of the meaning of the code, and a warning about misuse – and if it forces the user to listen and understand the message. For example, in an experiment testing secure password reset procedures, successful wording of a phone message included a statement like this:
“Warning! Someone asked to reset your Google password. I repeat: Someone asked to reset your Google password. If you did not ask for a password reset code, press 3. Otherwise, press 4.”
Checklist – The Best cyber security strategies and Practices Against PRMitM
According to research published about PRMitM, following these fundamental rules when designing password reset processes will help protect users:
-
Password-reset messages should include the name of the sending website, a clear explanation that the code is for password reset, and a warning not to give the code to any person or website.
-
When sending a code over SMS, use a link-via-SMS (LVS). Sending a detailed SMS with a long link overcomes the limitations of a clear-text code. It requires the attacker to ask the victim to copy the link to the malicious website, which is unusual; and it makes it more likely the victim will notice the rest of the message and be alerted that someone is trying to reset the password.
-
The password reset message (SMS, phone call, or email) must be translated into the correct language. This means these messages must be translated into every supported language.
-
When testing a password reset process, make sure to test separately for every supported language.
-
When a password reset request is sent, notify the user by both email and phone.
-
When a link or code is sent that enables a user to reset a password, the link should be valid for a maximum of 15 minutes.
-
The ten most popular websites support password reset using the user’s email account. Most also allow password reset using a phone, as an alternative. When a user has multiple ways to reset passwords, some of which are less secure – disable the less secure options. Similarly, if a user does not have a secure option, contact the user and ask for information that allows secure password reset in the future.
-
Obtain multiple details about the user before sending the password-reset message. This eliminates the possibility of launching an attack just with a single piece of information, such as a phone number.
Bottom Line: There’s a Right Way – and a Wrong Way – to Do This
The link-via-SMS approach to password reset that was used in the PRMitM study caused ALL participants to detect and thwart the attack. This is just one, small example of how redesigning password reset processes carefully – in ways that increase security – can be effective in eliminating PRMitM attacks. If you still have concerns about MitM attacks and want to speak to one of our experts, contact us and we’ll set up a call.


