To be competitive and support business growth, organizations relying on Operational Technology (OT) ecosystems must adopt new technologies – integrating innovations & enhancements with legacy systems to obtain increased volumes and business growth.
Organizations need to take advantage of the capabilities provided by Industry 4.0, including the integration of machine learning and automated processes into industrial processes, in order to increase productivity and reduce costs. Yet, these advances come at a price: the increased risk that comes with technical enhancements.
Strategies must be developed by Security Operations Centers (SOCs) to detect and respond to new cyber-attacks that leverage weaknesses in converged IT/OT networks - which are becoming increasingly common, as well as increasingly sophisticated.
IT vs. OT Security Architectures
Traditionally, the Information Technology (IT) and Operational Technology (OT) ecosystems have been built in separate siloes.
IT and OT networks require entirely separate approaches with regard to safety and security. As we all know, Information technology involves computers and networks, with the primary asset being data; the primary job of IT security is to protect confidentiality. In contrast, the top priority of OT security is safety, closely followed by continuity of service.
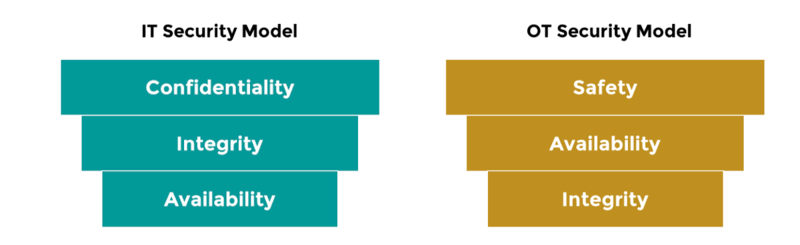
OT networks typically involve the use of legacy hardware and software. Because they are generally deployed over a period of time, OT systems have usually resulted in a complicated ecosystem of devices, hardware, and software, industrial elements, etc.
Monitoring all the traffic within such a distributed setup, providing visibility into all devices, and protecting so many varied components is both complex and delicate - especially when considering the need to keep the system permanently operational. In contrast, an IT network can be temporarily shut down for security updates.
An important point to note here with regard to OT systems is that even a few minutes of a plant shutdown can result in huge business losses and - where the system in question supports critical services (such as a water purification plant or electricity generation, for example) - it can impact the safety of millions of people.
The Convergence of IT and OT Environments
Historically, OT plants and systems were kept in their own silos - what we generally call “air-locked,” i.e., keeping OT systems protected from outside threats and safe from harm, and thus, ensuring that they are continuously operational.
Today, it is essential for IT security experts to align with OT security standards when the two converge.
Everything shifted about a decade ago with the advent of Industry 4.0. Integrating machine learning and automated processes into industrial technology meant connecting IT environments with OT environments - which were previously air-gapped for security reasons.
The convergence of the two systems became even more necessary as technology improved. As the need for interconnectivity increased, this convergence opened OT systems to many more cyber threats - increasing the criticality of OT security, as cybersecurity breaches became more common particularly in OT-oriented organizations such as manufacturers and centers providing critical services. Thus, cybersecurity measures to protect OT systems developed in response to the ongoing evolution of Industry 4.0.
Today, it is essential for IT security experts to align with OT security standards when the two converge. Likewise, those working in OT security must adopt IT security protocols. The convergence of IT and OT – which allows organizations to streamline processes, improving efficiency, and saving money – is expected to become almost universal, and therefore, it is no longer logical to view these systems as discrete or independent.
As the need for interconnectivity increased, this convergence opened OT systems to many more cyber threats - increasing the criticality of OT security.
At the same time, integrating OT and IoT security into the mandate of security operations involves much more than simply extending IT security solutions and staff responsibilities to include industrial networks. The convergence requires someone with the experience and skills to support both the transition and the ongoing operations.
The Importance of Securing OT Environments
Before you can even start planning to integrate OT and IT security monitoring, it’s essential to secure the OT environment. Securing the OT environment involves reviewing that your processes and security controls are in place, and you have technologies that can help monitor, detect, and mitigate possible security attacks. But perhaps most importantly, you must ensure that the people in your organization are well trained regarding security processes and are aware of the workflows to be followed in case of an attack.
Paying attention to securing the OT environment has become particularly important more recently, for the following reasons:
- Increase in OT-related incidents - The number of cyber-attacks on critical infrastructure and strategic industrial assets has dramatically increased. Attacks have included attempts to disrupt operations and compromise intellectual property.
- Increase in Zero-Day vulnerability disclosures – Various organizations have been reporting an increasing number of new vulnerabilities found in different protocol vendors - e.g., ABB, Rockwell Automation, etc. Given this constant reporting of vulnerabilities, organizations feel under constant attack and are losing visibility of their attack surface.
- Increase in government regulations, frameworks, and direct involvement - In response to the increase in attacks, governments around the globe are intensifying their regulatory oversight and breach reporting requirements. Governments are particularly concerned about advanced persistent threats to OT environments, particularly when the environment under attack is viewed as critical infrastructure. Today, organizations must adhere to the regulatory compliance requirements of various government agencies around the globe such as IEC 62443.
- Increased connectivity – Leveraging automation and other industry 4.0 components gives a competitive advantage to an organization on the business front. But with increased connectivity, the exposure of OT to the internet and IT world cannot be ignored. The necessary security controls must be put in place.
- The difficulty of having 2 CISOs for 2 business verticals – Most enterprises are starting to realize that security, whether it is IT or OT, needs an enterprise-level focus. Where security is involved, historical IT and OT functional differences are becoming a liability. Due to design, age, or function, the unique requirements of OT systems now add to IT security concerns in ways that can no longer be ignored. Modernization efforts bring discussions about risk, security, and safety to the forefront. As a result, leading organizations are starting to incorporate OT security requirements into their enterprise risk management efforts - adopting an integrated security strategy across IT and OT environments.
- Use of emerging technologies - Advances in robotics are enabling remote operations in hostile or off-shore locations, with fewer humans on-site. At the same time, the emergence of 5G is having widespread implications, because of its effects on connected systems. All these advancements come at a price - and that price is the cyber risk. It is increasingly important to ensure that we have the required security controls in place.
You must ensure that the people in your organization are well trained regarding security processes and are aware of the workflows to be followed in case of an attack.
Key Advantages of an IT/OT Integrated SOC
Organizations set up SOCs to prevent, detect, and respond to cyber threats and incidents. Often, having a SOC also fulfills regulatory requirements.
On the IT side, we are long accustomed to building and running SOCs. And now, many organizations have started extending SOC capabilities to the OT side of the business, as well, and are running an integrated IT/OT SOC. This can be helpful in the following ways:
- Better visibility and control for CISO and CIOs – A single function and fusion center for viewing IT security operations – which includes SIEM(s), EDR, Threat Intel tools, etc. - as well as OT security operations, which includes the central console and various servers and collectors installed in plants at locations across the globe.
- Proactive security – An integrated SOC team can proactively handle incidents - and can collect response activities for analysis and reinforced learning, leading to a continuous reduction in response time and associated exposure risk.
- Detect threats faster – Most cyber-attacks on OT systems originate on the IT network and involve multiple steps, in an elaborate cyber kill chain. An integrated IT/OT SOC allows you to stop threats at earlier stages.
- Faster response times – An integrated SOC means that ONE team handles both the IT & the OT SOC and you avoid the handovers, delays, or miscommunication that can take place when there are two different teams, each with its own scope and objectives.
- Efficient use of resources – We all acknowledge the shortage of skilled resources in the field of security and the investments required for security technologies. It is more cost-effective to include OT and IT threat monitoring within one comprehensive SOC than to have multiple SOCs. By keeping your SOC lean, that is, utilizing the same monitoring and incident response team and resources, you can be more efficient in your operations.
- Leverage your people – their strengths and experience – An organization can reduce its skills gaps and improve the productivity of its teams by training the IT team to handle OT setups, architectures, and processes - and by teaching the OT team better IT cybersecurity skills.
Work with Experienced Professionals to Establish Your Integrated IT/OT SOC
Some advanced MSSPs, such as CyberProof, work with leading OT security product companies such as Radiflow. Here at CyberProof, we have helped several of our customers build an integrated IT/OT SOC using our SOC service delivery platform – the CyberProof Defense Center (CDC) Platform - which provides a single screen view to both IT & OT Security Operations. Typically, our high-level architecture includes:
.png?width=996&name=Security%20services%20Diagram-2-01%20(2).png)
Typical integrated architecture of an IT/OT SOC
Advanced MSSPs like CyberProof can provide organizations with services for an integrated IT/OT SOC such as:
- Asset visibility & Intelligence
- Monitoring & detection of threats
- Threat intelligence
- Vulnerability management
- Unidirectional gateways
- Risk assessment in line with the IEC 62443 standard
The CyberProof Defense Center (CDC) Platform provides a single screen view to both IT & OT Security Operations.
Moreover, advanced MSSPs play a key role as more applications, service and infrastructure migrate to the cloud. SOC teams are increasingly adopting solutions like Microsoft Azure Sentinel and Microsoft Defender for Endpoint – and working with an expert team in integrating all of the various aspects of your security operations allows you to reduce the time to respond and mitigate the damage that could be caused by an attack.
Interested in learning how the CyberProof’s experts can help your organization integrate your IT and OT SOC? View our datasheet or contact us today!


