In October, researchers found a complex EDR bypass technique used in BlackByte ransomware that evades EDR detections. Only a month later, similar tools were found that linked EDR bypassing to the financially motivated hacking group, FIN7 (Carbanak), that carried out a major ransomware campaign.
CyberProof’s Cyber Threat Intelligence (CTI) team has identified ties between threat actors related to these EDR bypass techniques, uncovering the covert mechanisms used by various ransomware gangs, what is motivating their attacks, and what protections can be implemented to bolster security against these custom techniques.
What new techniques are being utilized?
Researchers discovered a sophisticated EDR Bypass technique that was utilized by recent samples of the BlackByte ransomware.
In this BlackByte ransomware sample written in Go, the researchers discovered a notable evasion technique that efficiently bypasses EDR detection. As part of the new technique, the BlackByte ransomware operators identify the kernel version of the targeted system and then drop the vulnerable, legitimate RTCore64.sys driver into the AppData\Roaming directory. This driver is used by MicroStar’s MSI AfterBurner 4.6.2.15658, a widely used graphics card overclocking utility.
Furthermore, the dropped driver is vulnerable to CVE-2019-16098 – a high severity flaw (CVSS Base Score: 7.8) in the RTCore32.sys and RTCore64.sys drivers that could enable authenticated users to read and write to arbitrary memory, I/O ports, and MSRs. The flaw can be exploited for privilege escalation, code execution under high privileges, and information disclosure.
At this point, a new service with a hardcoded name is created, and the BlackByte payload starts abusing the arbitrary read-and-write vulnerability in the RTCore64.sys driver. This is done to remove the callbacks related to over 1,000 security products from the kernel memory. To bypass modern mitigations like Driver Signature Enforcement, the BlackBytes operators abuse a legitimate, signed version of the vulnerable RTCore64.sys driver. However, researchers were able to find multiple similarities between the open-source tool EDRSandblast and the EDR bypass implementation of BlackByte – suggesting that the BlackByte group has at least copied multiple code snippets from the open-source tool and reimplemented it into the ransomware.
Researchers discovered a sophisticated EDR Bypass technique that was utilized by recent samples of the BlackByte ransomware.
How FIN7 is leveraging EDR bypassing in ransomware attacks
A new analysis of tools used by the Black Basta ransomware operation has identified ties between the threat actor and the FIN7 (aka Carbanak) group.
When analyzing tools used by the ransomware group in attacks, researchers found signs that a developer for FIN7 has also authored the EDR (Endpoint Detection and Response) evasion tools used exclusively by Black Basta since June 2022.
In fact, further evidence linking the two includes IP addresses and specific TTPs used by FIN7 in early 2022 - and seen months later in actual Black Basta operations.
Researchers have found that Black Basta has been deploying a custom EDR evasion tool used exclusively by its members. In this case, an executable, “WindefCheck.exe”, displays a fake Windows Security GUI and tray icon that gives users the illusion that Windows Defender is working normally. However, in the background, the malware disables Windows Defender, EDR, and antivirus tools - ensuring that nothing would jeopardize the data exfiltration and encryption process of the ransomware.
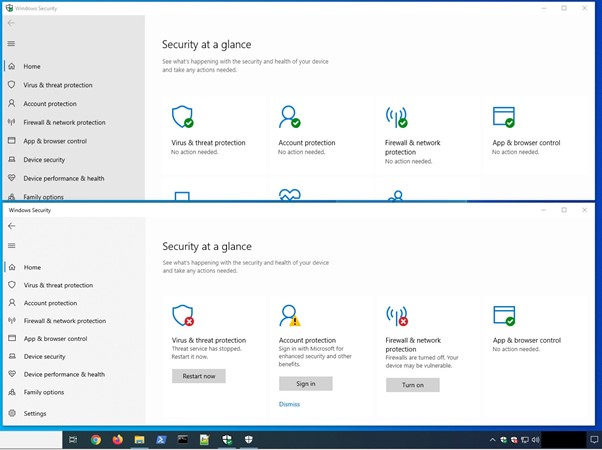
Figure 1: Fake Windows Security GUI WindefCheck.exe (top), and Legitimate GUI (bottom)
Further analysis shows that the Black Basta operations use a uniquely obfuscated version of AdFind - and exploit PrintNightmare, ZeroLogon, and NoPac for privilege escalation.
A new analysis of tools used by the Black Basta ransomware operation has identified ties between the threat actor and the FIN7 (aka Carbanak) group.
Identifying bypass techniques - before it’s too late
EDR bypass techniques are often employed to distract users from a malware attack taking place on their devices, leaving attack victims to uncover these mechanisms only after damage is done. Employing prevention tactics before bypass and ransomware attack techniques are put in place is critical to protecting your assets and minimizing the devastating impact of a ransomware attack.
Actionable tip: If you’re concerned about ransomware attacks, and you would like a list of specific Indicators of Compromise (IoC) that you can scan for within your environment, and implement in your security systems, make sure to reach out to our SecOps team.
To ensure that your endpoint is secured against these threats, we recommend implementing these prevention measures:
- Ensure that applications, drivers, and operating systems are running at the currently released patch level.
- Implement Indicators of Compromise (IOCs) into your security systems.
- Monitor and hunt for the vulnerable RTCore64.sys driver within your environment. Note that this driver is in fact legitimate and does not indicate malicious activity directly; therefore, such detection should be further analyzed to evaluate a true connection to the BlackByte ransomware.
- MD5: 2d8e4f38b36c334d0a32a7324832501d
- SHA-1: f6f11ad2cd2b0cf95ed42324876bee1d83e01775
- SHA-256: 01aa278b07b58dc46c84bd0b1b5c8e9ee4e62ea0bf7a695862444af32e 87f1f
- Ensure that legitimate drivers that are currently exploited in the wild by threat actors are block listed and/or monitored. It is also essential to keep track of the drivers installed on your systems and maintain a regular updating process.
Actionable tip: If you’re concerned about ransomware attacks, and you would like a list of specific Indicators of Compromise (IoC) that you can scan for within your environment, and implement in your security systems, make sure to reach out to our SecOps team.
Looking for strategies to implement preventative measures against EDR bypassing and ransomware infiltration techniques? Reach out here to speak to an expert.


