Defending an enterprise’s infrastructure successfully requires using multiple products that – when fit together effectively – create a comprehensive, multilayer defense.
As part of the process of selecting the right products for cyber defense, the question of Endpoint Detection & Response (EDR) vs. Security Information & Event Management (SIEM) may be raised – mainly because each system provides rule-based alerting and offers threat hunting tools that allow you to explore and query raw data that’s collected by agents.
But is only one solution needed? Are they mutually exclusive? Let’s explore some of the advantages and disadvantages of each approach.
Table of contents- EDR vs. Siem: Different Solutions, Different Purposes
- DATA COLLECTION AND HUNTING
- IOC AND IOA-BASED ENDPOINT DETECTION
- SO WHICH SHOULD YOU USE?
- GETTING THE MOST OUT OF YOUR INVESTMENTS
EDR vs. Siem: Different Solutions, Different Purposes
EDR and SIEM are designed to meet different goals and purposes. A next-generation SIEM like Azure Sentinel has the main goal of providing cloud-scalable security information and event log management.
Using this kind of next-generation SIEM, customers are able to aggregate data across the enterprise from all sources, including users, applications, servers, and devices running on -premises or in any cloud - allowing the review of millions of records in a few seconds.
A next-generation SIEM also can generate high-context alerts, reducing false positives and prioritizing escalations. And compared to traditional SIEMs, cloud-native SIEMs offer advantages including easier onboarding, faster deployment, and lower operational costs.
EDR has a different set of capabilities. It is designed to offer continuous detection and response at the endpoint against malware and threats, provide anti-ransomware capabilities, and detect file-less and “living off the land” (LotL) attacks.
Using this kind of next-generation SIEM, customers are able to aggregate data across the enterprise from all sources, including users, applications, servers, and devices running on -premises or in any cloud - allowing the review of millions of records in a few seconds.
EDR comes with a default set of behavioral detection rules that are created by high-level research teams and provide endpoint protection from day one. In addition, EDR supports custom rule mechanisms, and most EDRs provide threat intelligence-based detection.
From the SIEM side, EDR provides another log source out of many. But from the security analyst’s side, EDR is a powerful tool that provides both endpoint protection and advanced investigation and threat hunting capabilities.
EDR vs. siem: Data Collection and threat Hunting
While EDR only collects endpoint data, a next-generation SIEM has the advantage of running queries and hunting for data related to many components aside from the endpoint. It collects logs from additional layers including cloud and on-premise infrastructure, network, users, applications, etc.
A next-generation SIEM supplies tailor-made correlation and analytics rules. It effectively filters huge volumes of events and utilizes machine learning (ML) to identify any anomalies that may be hidden within acceptable user behavior.
Note that the SIEM agent collects endpoint events mainly from logs created by the operating system (Windows or Linux), which makes it a secondary recording system relaying information taken from another event creator. This is fundamentally different from the EDR agent, which is installed on both the user and the kernel space. The EDR agent collects its own raw data on endpoint files, processes, connections, and other security-related events – in addition to having prevention capabilities. Some of the data obtained by the EDR agent may overlap, but most of it provides significant added value in its own right.
A next-generation SIEM supplies tailor-made correlation and analytics rules. It effectively filters huge volumes of events and utilizes machine learning (ML) to identify any anomalies that may be hidden within acceptable user behavior.
edr vs. siem: IOC and IOA-Based Endpoint Detection (EDR)
A next-generation SIEM not only provides IOC detection, but also aggregates relevant data across the enterprise - allowing you to effectively carry out investigations and handle incidents. A SIEM can facilitate playbook management and provide query languages supporting the creation of rules for hunting, analytics, dashboards, and reporting.
The EDR’s activities start in a different space: using custom detection rules based on IOC data and behavioral detection data that allow detection of the most recent, most advanced threats relevant to your business. EDR also has prevention mechanisms and immediate response capabilities – manual and automatic – that allow organizations to kill processes, quarantine files, block IPs, delete persistency, and more. Because of these capabilities, EDR should be the first tool to load and to define an organization’s IOCs and custom detection rules.
So Which Should You Use?
Actually, the question of whether to use EDR or SIEM is not a real dilemma. Each of these solutions provides different benefits for your security operations.
Given the importance of advanced endpoint security to protect an organization from threats like ransomware (and other infections) – and the importance of managing data and security incidents detected by multiple sources – EDR and SIEM can work side by side to provide the most effective, multilayer defense for your organization.
Keep in mind, however, that both solutions require ongoing management and maintenance, such as: customized detection rules, security and feature policies, IOCs, behavioral whitelisting rules, and sensor management and upgrades – as well as managing the investigation of security incidents, and more.
Getting the Most Out of Your Investments
Using both EDR and SIEM requires investing security spend in both technologies. So, how do you ensure that you’re investing wisely, utilizing fully, and really getting the “bang for your buck”?
Working with a Managed Detection & Response (MDR) specialist like CyberProof helps make sure that you are using both your EDR and your SIEM technology optimally, while simultaneously lowering operational costs. MDR specialists help you implement the right solutions no matter how mature your cyber defense, offering organizations support with planning, design, implementation, configuration, and optimization of EDR and SIEM, based on each organization’s unique business and technical requirements.
MDR specialists handle continuous monitoring of EDR and SIEM security alerts – and maintain policies and custom detection rules based on the most recent threats across multiple industries by proactively conducting historical searches of raw data collected by agents.
Working with a Managed Detection & Response (MDR) specialist like CyberProof helps make sure that you are using both your EDR and your SIEM technology optimally, while simultaneously lowering operational costs.
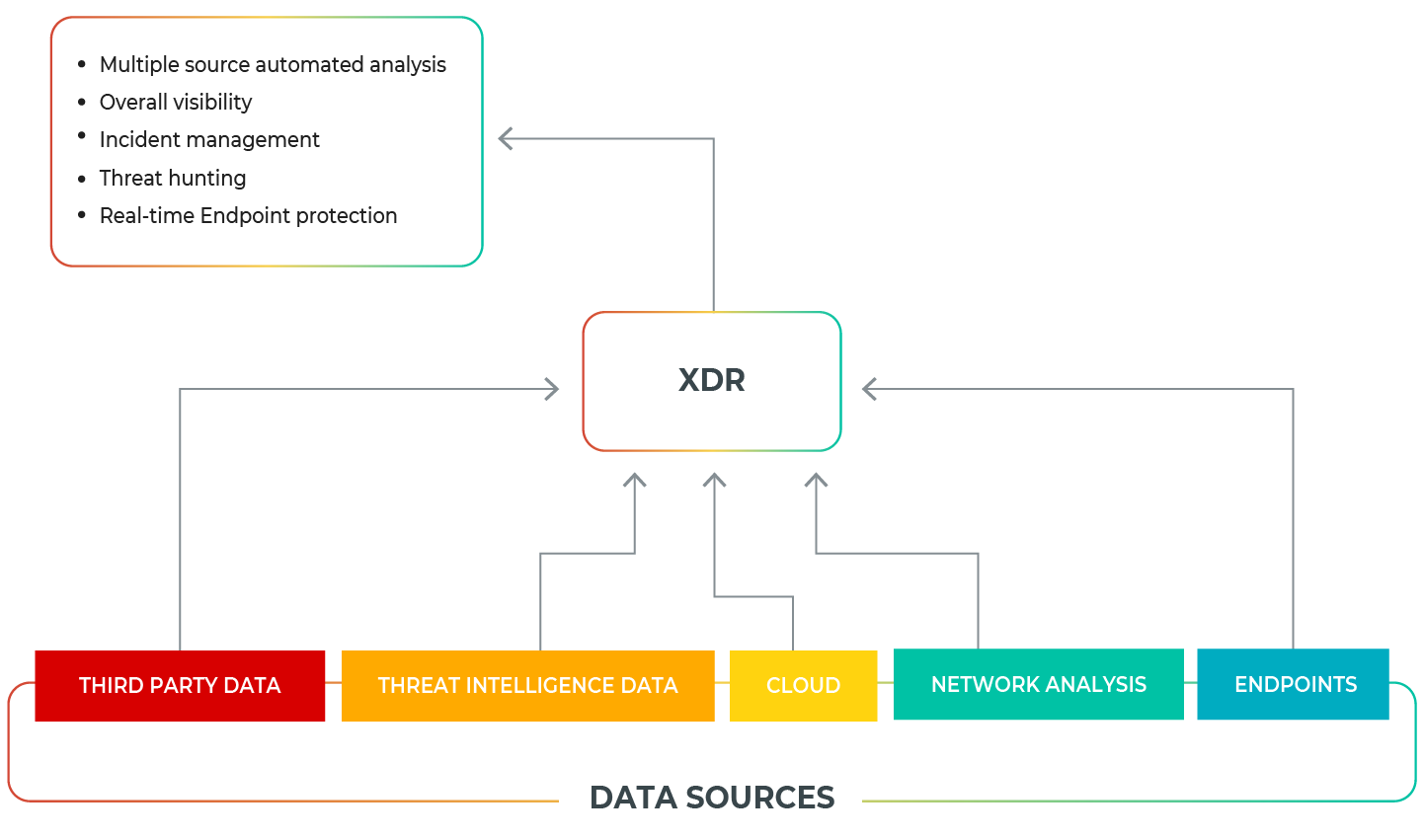
XDR multilayered prevention and remediation capabilities
The quality of MDR services reflects this ability to incorporate XDR visibility from endpoint, network, and security log data – an essential capability in picking up on threats that are otherwise missed and in analyzing data collection in a scalable manner.
If you want to speak to one of our experts and learn more about how to protect your organization, contact us today.


