This blog post is the third in a series about threat hunting by Shani Touitou, Incident Response and Threat Hunting Specialist. To read the second blog in the series, click here.
Remote access tools are increasingly used as our world becomes more digitally connected. Companies are now able to operate networks of employees working globally by remotely connecting to an internal network. At the same time, threat actors manipulate these new technical capabilities to infiltrate into networks, potentially exposing data and sensitive material. After threat actors gain access to the internal network, they may attempt to exfiltrate sensitive data by leveraging remote access tools to avoid detection.
The use of Remote Access Applications can often be used for legitimate purposes, but are often exploited by threat actors to gain control of a victim’s computer, often for malicious purposes. Analysis of activity can indicate if a system is compromised by threat actors. CyberProof’s threat hunting team conducts such analysis in order to identify potential threats in our client’s systems.
What are NAS devices?
Network attached storage (NAS) devices are dedicated file storage systems that connect to a network, allowing for centralized data storage and file sharing within a network environment, both for corporations and individuals.
The versatility of these devices means they can be tailored to a wide range of needs, from simple home file storage to sophisticated business applications.
NAS devices typically have a large storage capacity that can be used to store significant amounts of data. This makes it easier for a malicious party to collect and exfiltrate large datasets and data can be moved to it without raising suspicion. Therefore, in business settings, using NAS storage devices without enterprise permission can introduce several security risks to an organization.
Description of the hunt
The recent news of the AnyDesk cyberattack that led to multiple data breaches prompted CyberProof’s threat hunting team to conduct an investigation for our clients, ensuring that the same techniques used in those attacks could not be re-exploited. Our team conducted a directive hypothesis based on suspicious usage of remote access applications in client networks.
The hunting procedure was conducted to detect the presence and behavior of any communication attempts from an AnyDesk.exe host to an external URL, which would then lead users to a service that allowed them to connect their network attached storage (NAS) device over the Internet without having to perform router configurations. The URL contains a unique identifier assigned to a specific NAS device by the issued service.
Identifying potential malicious activity in remote connections
The remote Access Capabilities using the AnyDesk application from the enterprise network on one side and accessing remotely on the other side using the NAS storage customized URL can be exploited by threat actors to access the data from outside the organization's network.
Threat actors can exploit remote access vulnerabilities by targeting systems like the AnyDesk application and NAS storage used within an enterprise network. By manipulating these remote access points, attackers can gain unauthorized access to data from outside the organization's network. This type of exploitation can lead to data breaches, as it allows cybercriminals to bypass network security measures and access sensitive information remotely.
To detect the presence of potential malicious activity within users of remote admin tools in a network, we employed this hunting query that focuses on use of external URLs. This query allows threat hunters to access all external URL access in a network, filtering out internal IPs and whitelisted websites:
let remoteadmintool = dynamic(["telnet", "ssh", "securecrt", "teamviewer", "dameware", "ammyadmin","logmein", "cygwin", “anydesk”,
, "putty", "Ncat", "Netcat" "cmd"]);
let FileNamesWithCommunication = toscalar(
DeviceFileEvents
| where FileName has_any (remoteadmintool)
| summarize make_set(FileName)
);
let InternalIPList = dynamic (["Reserved", "Private", "LinkLocal", "Loopback"]);
let RemoteUrlWhitelisting = dynamic (["ssh.dev.azure.com", "github.com"]);// add your customized whitelisting
DeviceNetworkEvents
| where InitiatingProcessFileName in (FileNamesWithCommunication)
| where ActionType != "ConnectionFailed"
| where RemoteIPType !in (InternalIPList)
| where RemoteUrl !in (RemoteUrlWhitelisting)
The risk of unauthorized NAS devices
An unauthorized NAS device is essentially a form of shadow IT, and the lack of visibility into its operations means it could be used extensively for exfiltration before being discovered. Additionally, NAS devices also introduce another security risk – that of third party vendors. NAS devices not managed by the enterprise may not be subject to the same security measures as official systems, such as network monitoring and data loss prevention (DLP) tools, allowing for stealthy removal of data. NAS services that are directly connected to the Internet can significantly increase security risks, as they widen the available attack surface. 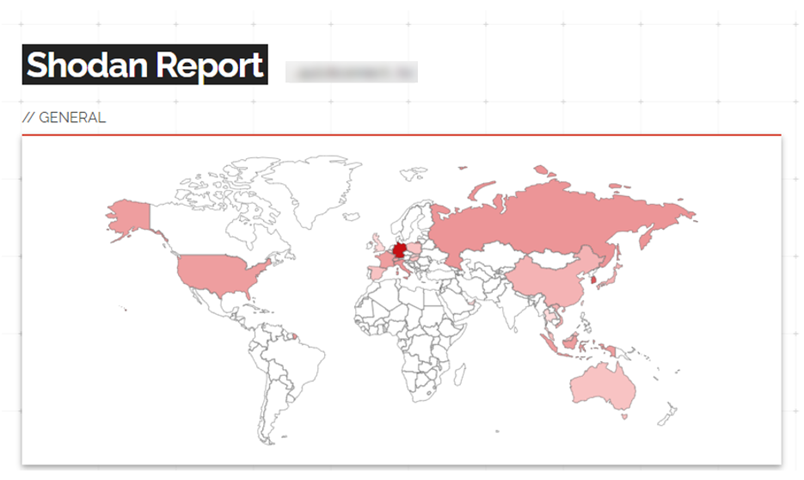
NAS storage links connected to a global vendor that are currently exposed
Best practices for preventing remote access attacks
Remote connections designed to appear legitimate can be easily missed by security products – human-led and proactive threat hunting can prevent that. Hunting adds a layer of security by that proactively identifies and mitigates sophisticated cyber threats, contributing to the strategic enhancement of the client's overall cybersecurity framework. This is particularly valuable in today's landscape where advanced persistent threats and sophisticated evasion techniques are constantly evolving.
There are two perspectives that need to be considered when developing security best practices for implementing NAS storage devices.
-
Internal and external vectors: Monitoring attack vectors internally and externally requires ongoing threat hunting and detection rule implementation. In the case of malicious remote access, threat actors can be working internally and exfiltrating data or working externally to access internally-stored company data. Internal security detection and monitoring must take place, such as the detection of communications with URLs containing remote access to the NAS storage system, or detection of remote access applications communicating with a URL of the NAS device.
-
Security standards for third-party NAS storage use: The use of NAS devices in an organization may be part of a legitimate backup and data preservation process. Alternatively, it can be used for data exfiltration of internal employees or be part of the attack strategies of malicious threat actors. In all cases, NAS storage use should be monitored and restricted by strictly-enforced policies, including:
-
Limiting access to NAS URLs that are not associated with the organization
-
Monitor use of NAS devices to ensure that they are organization-approved
-
Remote connections designed to appear legitimate can be easily missed by security products – human-led and proactive threat hunting can prevent that.
Our recommendations
CyberProof’s recommendations for preventing and mitigating an attack by a potentially malicious remote user:
-
Verify communications with any NAS devices with end users to ensure non-malicious intentions of data transfer using the platform.
-
Implement network segmentation and security controls that limit access to sensitive data.
-
Utilize DLP strategies and monitor network traffic for unusual patterns that may indicate data exfiltration.
-
Enforce strong access controls and authentication mechanisms.
-
Educate employees about the risks and policies related to using unauthorized devices for storage or data transfer.
Want to learn more about how proactive threat hunting can be used to mitigate risk? Contact us.
This blog post is the third in a series about threat hunting by Shani Touitou, Incident Response and Threat Hunting Specialist. To read the second blog in the series, click here.

.png?width=686&height=200&name=blog_banner_copy%20(002).png)

