With its data-driven analysis of the current cyber security threat landscape, this year’s Verizon Data Breach Investigation Report (DBIR) is the most extensive to date – covering 86 countries based on data from 73 contributors, the highest number since the report first was launched in 2008.
The 2019 report covers the state of cyber security threats for enterprise with its analysis of approximately 1.5 billion data points of non-incident data. And, for the first time, it also includes information about security incidents reported to the FBI’s Internet Crime Compliant Center (IC3).
Here are some of DBIR 2019’s major findings:
Key Insights
- Increase in the number of attacks on the C-Suite – In 2018, senior executives were 12 times more likely to be a target of social incidents and 9 times more likely to be a target of social breaches.
- Drop in attacks on human resources – 2018 saw 6x fewer attacks on human resources professionals, correlating to the practical disappearance of W-2 scams from DBIR’s dataset.
- Chip & pin is making a difference – In payment card related breaches, 2018 saw fewer physical terminal compromises and more web application compromises. In retail, it’s stark: PoS (Point of Sale) breaches decreased by 10 since 2015; breaches of Web Applications (like Magecart) became 13x more likely.
- Median loss due to business email compromise (BEC) attacks is a few thousand dollars – which doesn’t sound so bad. The downside is that there are the same number of attacks with losses below the median as attacks with losses above the median (going up to $100 million).
- Increase in cloud-based compromises – More companies sharing and storing information in the cloud means greater risk. Compromised email accounts and cloud misconfigurations (“Miscellaneous Errors”) led to the exposure of at least 60 million records.
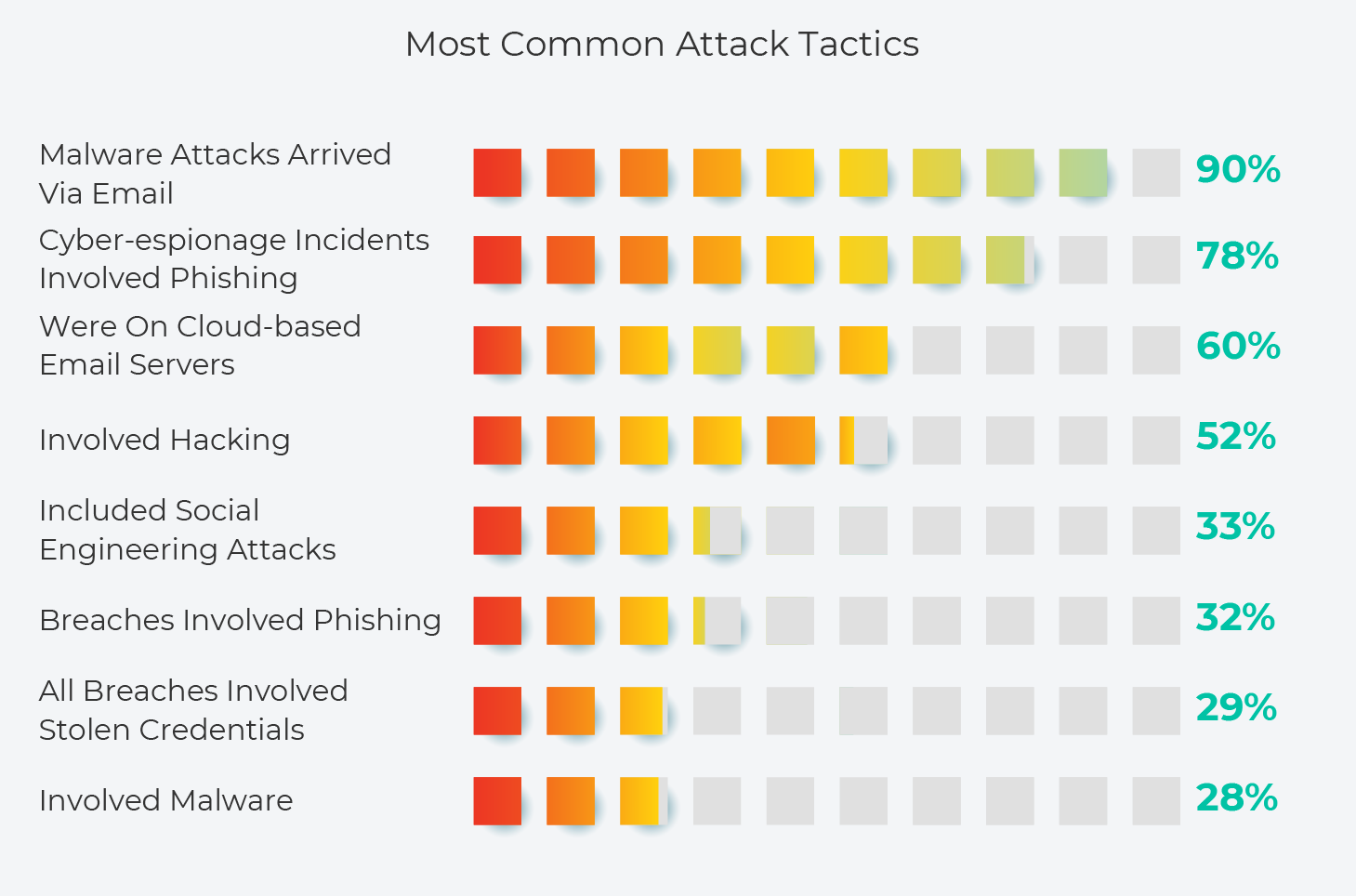
Most Common Attacks
- Ransomware attacks are still common, accounting for 24% of incidents where malware was used – and ranking #2 in most-used malware varieties. Ransomware is now so commonplace that it’s less frequently mentioned in specialized media, except in cases with high profile targets.
- 28% of attacks involved malware, and 90% of malware attacks arrived via email.
- 29% of all breaches involved stolen credentials.
- Phishing was involved in 32% of breaches and 78% of cyber-espionage incidents.
- 60% of web application attacks were on cloud-based email servers.
- Most email threats and BEC attacks resulted in data breaches only because multi-factor authentication had not been implemented.
- 52% of cyber attacks involved hacking.
- 33% of cyber attacks include social engineering attacks.
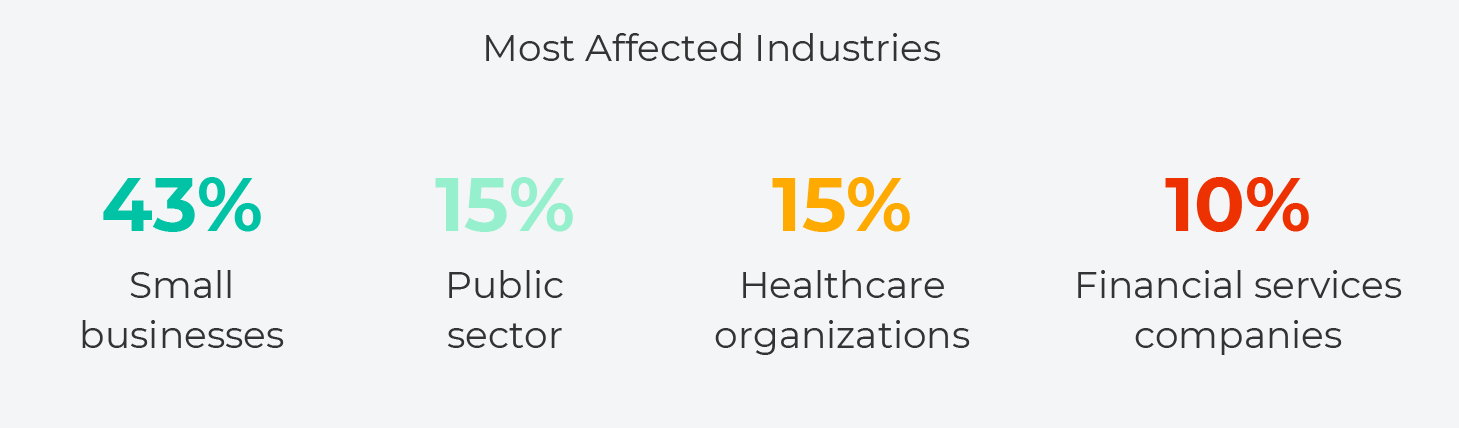
Industries Most Affected
- 43% of data breaches involved an attack on small businesses
- 15% of breaches involved public sector entities
- 15% involved healthcare organizations
- 10% involved financial services companies
Spotlight on Healthcare
Because of HIPAA regulations, healthcare is mandated to report any breach that occurs. There is higher reporting rates in healthcare than in other industries, as a result – and this needs to be noted when considering the report’s results.
For example, all healthcare ransomware infections are reported as a breach. Thus, while the statistics for ransomware across all industries is 24% of attacks, within the healthcare industry it is much higher – 70%. In other industries, one can assume that the real rate of ransomware attack is likely to be higher than what was publicly reported.
Shifts in Hacker Motivation
So, what’s behind these attacks? Here’s some of the reasons:
- 71% of attacks are financially motivated; and financially motivated cyber attacks are
increasing across the board. - Espionage is the second greatest motivating factor. Cyber-espionage related data breaches
increased from 13% of breaches in 2017 to 25% in 2018. - Nation-state attacks increased from 12% of attacks in 2017 to 23% in 2018.
DBIR documents variations in motivation per sector. The educational services sector, for example, saw a significant increase in attacks that were financially motivated (80%). In the public sector, in contrast, cyber-espionage rose – though nearly 47% of breaches were not discovered until years after the initial attack.
New Threat Sources
According to DBIR, 69% of breaches involve external threat actors, while 31% involve insiders. Healthcare is the exception to this: Of all the industries analyzed, healthcare is the only one in which there were a greater number of insider attacks (60%) than external (40%) attacks. DBIR includes these additional stats:
- 39% of all attacks are initiated by organized criminal groups.
- 23% of threat actors are nation-state or state affiliated.
Long-Term Trends
Verizon breaks incident types into nine categories and lists how frequently they occurred throughout 2018. This year’s top categories were:
- Privilege misuse
- Denial of service
- Crimeware
For the sake of comparison: The top 3 incident types in 2014 (when Verizon first used these categories), were miscellaneous errors, crimeware and privilege misuse – which illustrates the extent to which the types of attacks have shifted over time.
The Path of Least Resistance
Cyber criminals are opting for the path of least resistance. This trend, which is documented in the report, fits in with the growth in attacks on C-suite executives. C-suite executives have high-level privileges, so their credentials are valuable. They also tend to be pressed for time and therefore may be more likely to quickly approve a suspicious email.
The path to obtaining money from C-suite executives is simple: Threat actors can, for example, hack into a C-suite email account and use it to send a wire transfer request – which is much quicker than implementing complex hacking schemes. The growth in these kinds of attacks illustrates how important it is that employees of all levels receive regular training in security awareness.


