Threat actors utilize a wide variety of tactics and tools to gain access to a target network – frequently using the network’s endpoints as entry points to reach the organization’s “crown jewels.” More specifically, attackers are increasingly breaching a network by leveraging network vulnerabilities at the endpoint. Partly, this is because of how advanced persistent threats - which don’t use signatures - are able to evade traditional antivirus solutions, which don’t identify them as malicious.
Endpoint Detection & Response (EDR) solutions were developed to address this issue, providing the necessary visibility to spot advanced persistent threats by identifying abnormal behaviors and responding directly at the endpoint. EDR solutions generate very rich information about processes, actions, registry data, network connections, script analysis, file access, command lines, and more – providing organizations with a whole new level of visibility for threat detection and forensic investigation.
Moving from traditional security solutions to endpoint security is a big jump. As a result, many organizations struggle to take advantage of their investment in EDR technologies.
However, moving from traditional security solutions to endpoint security is a big jump. As a result, many organizations struggle to take advantage of their investment in EDR technologies. Let’s have a look at some of the key challenges organizations are facing in transitioning to endpoint security - and touch on ways to overcome these issues to leverage EDR technology optimally.
1. There’s an Overwhelming Amount of Data
EDR’s biggest benefit is that it provides a wealth of information. But that is also its biggest challenge. Due to the large quantity of data, knowing what to look for and configuring the EDR platform to protect you from the right threats can be a daunting task. Validating that a handful of alerts are actual threats can also take a lot of time – time that should really be devoted to responding to and mitigating the most serious incidents.
To interpret this data rapidly and effectively, a security team needs someone on board with prior experience and in-depth knowledge of EDR technologies – otherwise, it’s easy to get lost in all the information.
Working with a Managed EDR service provider like CyberProof can help organizations analyze the data and support faster, more effective threat detection.
That’s where Managed Detection & Response service providers come in. Working with a Managed EDR service provider like CyberProof can help organizations analyze the data and support faster, more effective threat detection.
2. Not All Attacks Can Be Prevented
Attackers are constantly reinventing themselves – creating new tactics and techniques, and releasing new variants of their malware. As a result, no organization is 100% secure.
But with the right combination of experience, skill, and ongoing development – the size of this gap can be kept to a minimum. This requires security teams to work continuously to create, test, and develop new uses case content and endpoint security policies.
One of the issues security teams face is that although EDR solutions come with threat hunting capabilities, security teams are not able to take full advantage of them. There’s either not enough time to hunt beyond what has already been detected – particularly as EDR creates such an overwhelming quantity of data – or they don’t have accurate and well-defined leads, based on which they can conduct their hunts. To address this, we recommend using a combination of techniques including retro-hunting for known endpoint IOCs, threat intelligence-driven hunting (MITRE ATT&CK techniques and tailored threat intelligence reports), incident-driven hunting (incidents affecting companies like yours), and behavior analysis (using mass amounts of data to form baselines and uncover anomalies).
3. Continuous Tuning is an Essential Part of the Process
Because EDR solutions have granular capabilities, configuring them requires a careful and ongoing process of calibration. For example, testing the endpoint security policies and updates in a red lab environment on an ongoing basis against relevant endpoint threats is important and can be used to validate the configuration.
A key goal of the configuration process is improving a system’s ability to distinguish between true positives and false positives. Sometimes, there is so much similarity between legitimate and malicious activity that malicious indicators are detected as clean; yet an EDR system that is carefully fine-tuned can distinguish between false positives and true positives. We, therefore, recommend doing the following:
- Give your EDR solution time to detect false positives before activating prevention capabilities – as this will reduce alert fatigue.
- Adjust endpoint security policies and profiles in stages.
- Search for suspicious activity in indicators such as command lines, admin account activity, executions from Temp folders, parent-child relations, etc.
- Test EDR updates before putting them into production to avoid security bugs in new releases.
It is the human analyst – not an EDR platform – who makes the final call regarding what is a true positive.
Be aware, however, that because the attack surface is constantly changing – EDR configuration must be updated and validated continuously to ensure that new threats are identified. Bottom line: It is the human analyst – not an EDR platform – who makes the final call regarding what is a true positive. A human analyst shapes responses provided by the technology – prompting it to make ever-more-accurate assumptions going forward.
The analyst’s skill and in-depth familiarity with an organization’s activity – i.e., with an operating system (OS) internals and structure – is necessary to triage the data. Extensive knowledge of fileless and living off-the-land attacks is also important, as is comprehensive information about attackers. It’s this combination of knowledge that allows analysts to accurately spot when logged activity represents a deviation from normal OS behavior.
4. Cutting Corners Hurts Threat Detection
Healthy EDR management can perhaps best be visualized as a cycle:
- Configuration: Properly setting up the configuration requires a significant investment of time.
- Testing: The better the configuration, the better the possibilities for testing. When the configuration is done too quickly, it also limits the efficacy of the testing process.
- Continuous Adjustment: As vendors add new features and detection methods to an EDR platform, these should be tested in a playground or lab environment before being implemented in production.
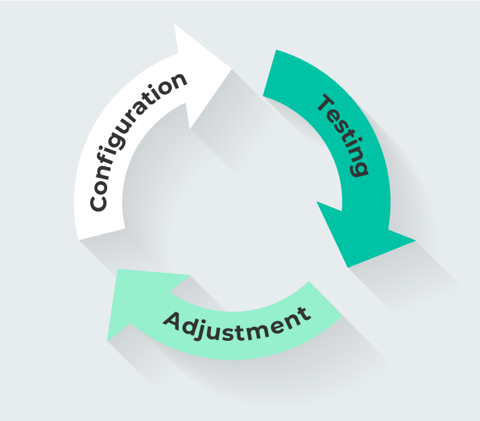
Each of these steps has an impact on the next step. If the system configuration is not fine-tuned, for example, testing becomes less effective – which in turn means that the system will generate too many alerts (both true positives and false positives). With the increase in noise, true positives tend to get missed – and this leads to security incidents.
If your organization is not working with skilled EDR analysts, you can end up in a vicious cycle: a poorly configured platform with limited testing that is less effective at threat detection.
Managing this kind of process requires having skills with EDR – and it takes time to gain these skills. If your organization is not working with skilled EDR analysts, you can end up in a vicious cycle: a poorly configured platform with limited testing that is less effective at threat detection.
5. Use Case Development is Essential
EDR tools are designed to help you detect security issues at the endpoint. But once an issue is detected – what next?
That’s where use case development comes in. A use case helps the analyst determine exactly which assets need to be protected, and which attack scenarios put these assets at risk – and then supplies a process, along with relevant content to detect and respond to those types of threats.
For a lot of EDR technologies, the default behavior is either to separate the machine from the network or to do nothing at all. But ideally, we want to isolate a process – not just to shut down a machine. We can develop use cases for EDR that are continuously updated and involve a much greater range of responses.
Agile EDR use case development starts out by asking these questions:
- What assets do I want to protect?
- Which types of attacks do I need to monitor?
- What detection gaps do I need to fill?
- How should I respond, and how quickly?
- What use case content do I need to define and maintain?
We can then package the content as a Use Case Kit containing the relevant detection rules, response playbooks, integrations into third-party technologies and level of automation required.
Use cases can provide a structured approach to detecting and responding to threats. They can support agile, risk-driven processes, and provide pre-determined responses while keeping up with the pace of change.
Enhancing Visibility and Threat Detection
EDR is a powerful technology for improving and hastening threat detection in endpoints, but it can also be overwhelming to manage given the depth of raw data it collects. EDR solutions leverage AI and ML, yet they require human expertise in optimizing the configuration, managing data and results, and knowing how to respond. EDR also requires human-based input in the form of tailored threat intelligence.
EDR solutions leverage AI and ML, yet they require human expertise in optimizing the configuration, managing data and results, and knowing how to respond.
Because of the complexity of configuring, testing, and improving endpoint security, it’s not unusual for organizations to invest in an EDR platform but then use only a small part of its capabilities. It’s therefore important to have resources and agile processes in place that can manage and optimize the EDR platform, leverage it fully as part of your security operations, and develop and tune use cases to ensure rapid and effective threat detection at the endpoint.
Interested in learning more about how CyberProof’s Managed EDR experts can improve your organization’s threat detection? Contact us today.


